For most visitors to Florida, going on a ‘tour’ usually means a trip to Disney World to meet Mickey and friends. Or perhaps a boat trip through the swamps.
But at Zero Trust World in Orlando this year, ThreatLocker’s security specialist, Collin Ellis, took IT managers, services providers, (and a TI journalist) on a journey through what is sometimes labelled the swamp of the internet – a deep dive into the Dark Web.
Threat intelligence manager Ellis took the stage at the conference to deliver an eye-opening presentation on the realities of the Dark Web.
Given the nature of the conference, this tour was presented through a ‘Zero Trust’ lens. Zero Trust is a cybersecurity framework that assumes no user or device—inside or outside a network—can be trusted by default, requiring continuous verification and strict access controls to minimise risk.
According to Ellis the tour is designed to help companies and MSPs understand what they are dealing with on the other side of the internet and seeks to answer the fundamental question of ‘why’ security is so crucial.

Collin Ellis ThreatLocker
The name ‘Dark Web’ itself carries a negative connotation. Originally developed for secure, anonymous communication by government agencies, it has since evolved into a space where lawful and unlawful activities coexist.
While often associated with illicit markets, cybercrime, and stolen data, it also serves as a sanctuary for journalists, whistleblowers, and activists operating under oppressive regimes. The Dark Web itself is neutral—it is simply a tool shaped by those who use it.
Accessing the Dark Web: Tails for safe browsing
Ellis detailed the logistics of safely accessing the Dark Web, recommending Tails OS, a Linux-based privacy-focused operating system that runs from a USB or DVD. It utilises the Tor network for encrypted and anonymous internet access, leaving no trace on the host computer.
“You can use it straight from the computer, but I prefer using a USB. This means that if at any point I feel like I’m being attacked or targeted, I just pull the USB out and everything drops,” Ellis explained.
While not completely foolproof, Tails remains one of the most secure ways to browse the Dark Web. Though tracking a user is possible, it would require significant resources and effort, Ellis added.
Constant change in the Dark Web landscape
According to Ellis, one of the biggest challenges of the Dark Web is its ever-changing nature. Unlike the traditional internet, which remains relatively stable, Dark Web sites, commonly referred to as ‘onion’ sites, are constantly shifting.
These sites are accessed via the Tor browser using “onion” addresses, which are not indexed by traditional search engines.
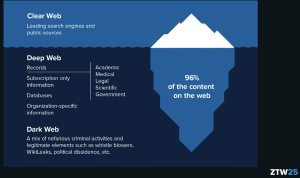
Dark Web Infographic
To navigate this landscape, users need a guide. Ellis highlighted resources like Darkweblinks.com – which can be found on the regular internet – which provides insights into active marketplaces, as well as ransomwaregangs.org, which offers intelligence on cybercriminal activities.
Another key resource is The Hidden Wiki, a frequently updated directory of Dark Web sites, which serves as a useful starting point for first-time explorers.
Ellis emphasised that merely accessing the Dark Web is not illegal; rather, it is the activities conducted there that determine legality. Even government agencies, including the CIA, maintain onion sites for secure communications.
The business of cybercrime: Hackers for hire
A particularly shocking revelation was how structured and organised the cybercriminal economy has become. Cybercrime is no longer just the domain of rogue hackers; it has evolved into a full-fledged industry with services for hire.
Ransomware gangs, social engineering experts, and exploit sellers operate like legitimate businesses, complete with customer reviews.
During his demonstration, Ellis explored an outsourcing website used by hackers, where individuals offer services ranging from DDoS attacks for $400 per month to social engineering attacks for $450.
One hacker, ‘Vladimir,’ specialises in technical attacks, while another, ‘George,’ focuses on manipulating people. The ease of outsourcing these services makes it alarmingly simple for even non-technical individuals to launch cyberattacks.
He drew a comparison to Amazon, noting how cybercriminals rely on user reviews to gauge the effectiveness of illicit tools and services.
For instance, malware like Zeus, which steals banking credentials, can be purchased for as little as $14. Cybercriminals do not need to develop these tools themselves—they can simply buy them prepackaged and launch attacks with minimal effort.
Your data is already out there
Ellis issued a stark warning: “More than likely, your information is already out there.” Data breaches at major corporations—ranging from Verizon and AT&T to password managers like LastPass—have exposed vast amounts of user data.
When LastPass was breached in 2022, hackers gained access to encrypted vault data, putting millions of users at risk. Ellis argued that companies rarely disclose the full extent of their breaches, meaning that users often have more information exposed than they realise.
Ransomware groups like Clop also maintain leak sites (which can also be found on the regular internet) which showcase data stolen from victims.
Universities, businesses, and even government institutions have found themselves listed, often without their knowledge. Miami EDU, for instance, has been compromised since 2019, with financial data copied multiple times.
Ellis cautioned against attempting to download leaked data, as doing so is illegal. However, he demonstrated how easy it is to search for personal information using automated tools—many of which are identical to those used by legitimate cybersecurity professionals. “Think about it—some of you sell this as a legitimate service! Cybercriminals are just using the same tools.”
The reality of Zero Trust
The final takeaway from the Dark Web Tour was clear: Zero Trust is not just a concept—it is a necessity. Ellis underscored the importance of operating under the assumption that your data is already compromised.
Security measures should be locked down until explicitly needed. Personal devices should be secured as rigorously as work devices.
“If your banking institution gets breached and your information is exposed, what does that mean for you and your family? You are a walking target.”
Cybercrime is a booming industry, and the only way to stay ahead is by adopting a Zero Trust mindset, he claimed. Understanding how the Dark Web operates is not about fear—it is about preparedness.